You Might Have Missed: NSA Reforms, CIA Drone Strikes, and Benghazi

More on:
“Presidential Policy Directive/PPD-28: Signals Intelligence Activities,” White House, January 17, 2014.
When the United States collects nonpublicly available signals intelligence in bulk, it shall use that data only for the purposes of detecting and countering: (1) espionage and other threats and activities directed by foreign powers or their intelligence services against the United States and its interests; (2) threats to the United States and its interests from terrorism; (3) threats to the United States and its interests from the development, possession, proliferation, or use of weapons of mass destruction; (4) cybersecurity threats; (5) threats to U.S. or allied Armed Forces or other U.S. or allied personnel; and (6) transnational criminal threats, including illicit finance and sanctions evasion related to the other purposes named in this section. (page 4)
(3PA: Does anyone really believe that the NSA will only gather nonpublic signals intelligence on behalf of six missions?)
Loveday Morris, “Interview with Iraqi Prime Minister Nouri al-Maliki,” Washington Post, January 16, 2014.
What support is Iraq receiving from the U.S. and what more would they like to see?
To build the Iraqi army and protect Iraqi sovereignty we need heavy weapons, fighter jets, helicopters, air defenses, this is in the long term. But right now, to defeat al-Qaeda, we need medium weapons, and we need intelligence cooperation. We need drones to scan the desert, and right now that’s gradually happening with America.
Can you give specific details? Has the U.S. pledged more support?
We’ve received only Hellfire missiles, which are being used to fight al-Qaeda. We’ve received one wave and have been promised another. The other weapons we have requested we have not received yet. The surveillance drones we have used them once or twice in the desert. There is intelligence collaboration which is very important for us.
What kind of intelligence is shared?
It’s tapping al-Qaeda communications, finding their camps and places on the ground, observing their routes over the borders. We work together on that field but we need more cooperation. We have many agreements with other countries to share information, but on the U.S. side we have the Status of Forces Agreement, under that framework we are exchanging more information than with most countries.
(3PA: What specific missions are U.S. drones being used to support?)
Eric Schmitt, “Congress Restricts Drones Program Shift,” New York Times, January 16, 2014.
In an unusual move, Congress is placing restrictions on the Obama administration’s plan to shift responsibility for armed drones more toward the military and away from the C.I.A., congressional and administration officials said Thursday. Lawmakers inserted wording into a classified annex to the $1.1 trillion federal budget approved by Congress this week that would make it more difficult to transfer control over the drone campaign or the authority to carry out strikes.
But the measure, first reported on the Washington Post’s website on Wednesday night, is a rare move by Congress to dictate how covert operations like the drone program are carried out. It also reflects the simmering suspicion among many lawmakers on the Intelligence Committees that the military’s Joint Special Operations Command is not up to the task of killing terrorism suspects with Predator or Reaper drones, a notion the Pentagon rejects.
(3PA: Last April I called for the Obama administration to transfer CIA drone strikes to the Pentagon, still a needed reform.)
Darren Samuelsohn, “Public remains ‘all over the map’ on NSA tactics,” Politico, January 16, 2014.
Senate Intelligence Committee Chairman Dianne Feinstein (D-Calif.) said public opinion is off the mark because Americans are getting a skewed picture of the NSA programs. She slammed press coverage that “has been dramatically one way” against the surveillance activities, though she’s been writing op-eds and speaking out trying to correct the record.
“I think there’s enormous misunderstanding out there about what exactly is done,” Feinstein said in an interview. “I think there is a misunderstanding because I think people believe we’re collecting content, that we’re collecting what people say to each other on the phone and that is not correct. It’s very difficult.”
(3PA: Sen. Feinstein, during John Brennan’s February 2013 confirmation hearing, said that she was unaware of the United States’ policy of signature strikes. Yet, when it comes to the NSA’s surveillance program, Sen. Feinstein seems to think she is more well-versed than the American public and many other congressmen.)
“Cisco Annual Security Report Documents Unprecedented Growth of Advanced Attacks and Malicious Traffic,” Cisco, January 16, 2014.
Overall vulnerabilities and threats reached the highest level since initial tracking began in May 2000. As of Oct. 2013, cumulative annual alert totals increased 14 percent year-over-year from 2012.
“Review of the Terrorist Attacks on U.S. Facilities in Benghazi, Libya, September 11-12, 2012,” U.S. Senate Select Committee on Intelligence, January 15, 2014.
On June 6, 2012, Stevens recommended the creation of teams, made up of locally hired personnel, in Benghazi and Tripoli. The State Department attempted to create a team in Tripoli, but was unable to · difficult to find and clear appropriate personnel. (page 14)
On July 9, 2012, Stevens sent a cable to State Department headquarters requesting a minimum of 13 "Temporary Duty" (TDY) U.S. security personnel for Libya, which he said could be made up of DS agents, DoD Site Security Team (SST) personnel, or some combination of the two. These TDY security personnel were needed to meet the requested security posture in Tripoli and Benghazi. The State Department never fulfilled this request and, according to Eric Nordstrom, State Department headquarters never responded to the request with a cable. (page 15)
DoD confirmed to the Committee that Ambassador Stevens declined two specific offers from General Carter Ham, then the head of AFRICOM, to sustain the SST in the weeks before the terrorist attacks. (page 20)
With respect to the role of DoD and AFRICOM in emergency evacuations and rescue operations in Benghazi, the Committee received conflicting information on the extent of the awareness within DoD of the Benghazi [CIA] Annex. According to U.S. AFRICOM, neither the command nor its Commander were aware of an annex in Benghazi, Libya. However, it is the Committee’s understanding that other DoD personnel were aware of the Benghazi Annex. (page 26)
DoD moved aerial assets, teams of Marines, and special operations forces toward Libya as the attacks were ongoing, but in addition to the seven-man reinforcement team from Tripoli, the only additional resources that were able to arrive on scene were unmanned, unarmed aerial surveillance assets. (page 28)
The Majority believes that the terrorist attacks against U.S. personnel at the Temporary Mission Facility and the Annex in Benghazi, Libya, on September 11 and 12, 2012, were likely preventable based on the known security shortfalls at the U.S. Mission and the significant strategic (although not tactical) warnings from the Intelligence Community (IC) about the deteriorating security situation in Libya. (Additional Majority News, page 1)
Susan B. Epstein, Alex Tiersky, Marian L. Lawson, “State, Foreign Operations, and Related Programs: FY2014 Budget and Appropriations,” Congressional Research Service, January 3, 2014.
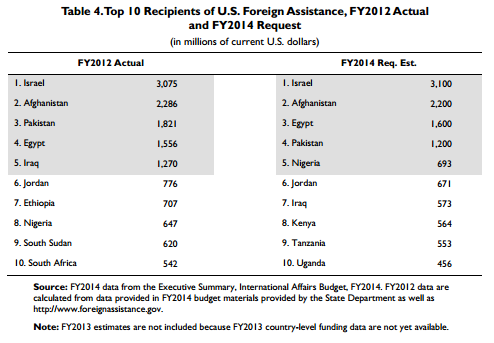
(page 10)
Craig Whitlock and Craig Timberg, “Border-patrol drones being borrowed by other agencies more often than previously known,” Washington Post, January 14, 2014.
Customs and Border Protection, which has the largest U.S. drone fleet of its kind outside the Defense Department, flew nearly 700 such surveillance missions on behalf of other agencies from 2010 to 2012, according to flight logs released recently in response to a Freedom of Information Act lawsuit filed by the Electronic Frontier Foundation, a civil-liberties group…In 2010, for example, Customs and Border Protection conducted 76 drone missions for other agencies. The next year, that number quadrupled, and it remained at nearly the same level in 2012.
Although the border agency has acknowledged that it flies drones for other law-enforcement departments, it has revealed little about the number and precise nature of the missions. Customs and Border Protection has a fleet of 10 unarmed Predator B drones. They are virtually identical to an Air Force drone known as the Reaper. Both are manufactured by General Atomics, a major drone producer based in Southern California…The FBI and other federal law enforcement agencies have their own drones, but they are more rudimentary than those operated by Customs and Border Protection. The Defense Department is prohibited from using its drones in the United States for law enforcement.
More on:
 Online Store
Online Store
